SPF, DKIM, and DMARC in 2024: Analyzing the Top 1M Domains
Have you ever wondered how widely adopted email authentication protocols such as SPF, DKIM, and DMARC are in 2024? We were curious, too. So, we downloaded the latest Tranco list, featuring the top 1 million domains, and wrote a script to dive deep into their DNS records. Here’s what we discovered.
SPF Insights
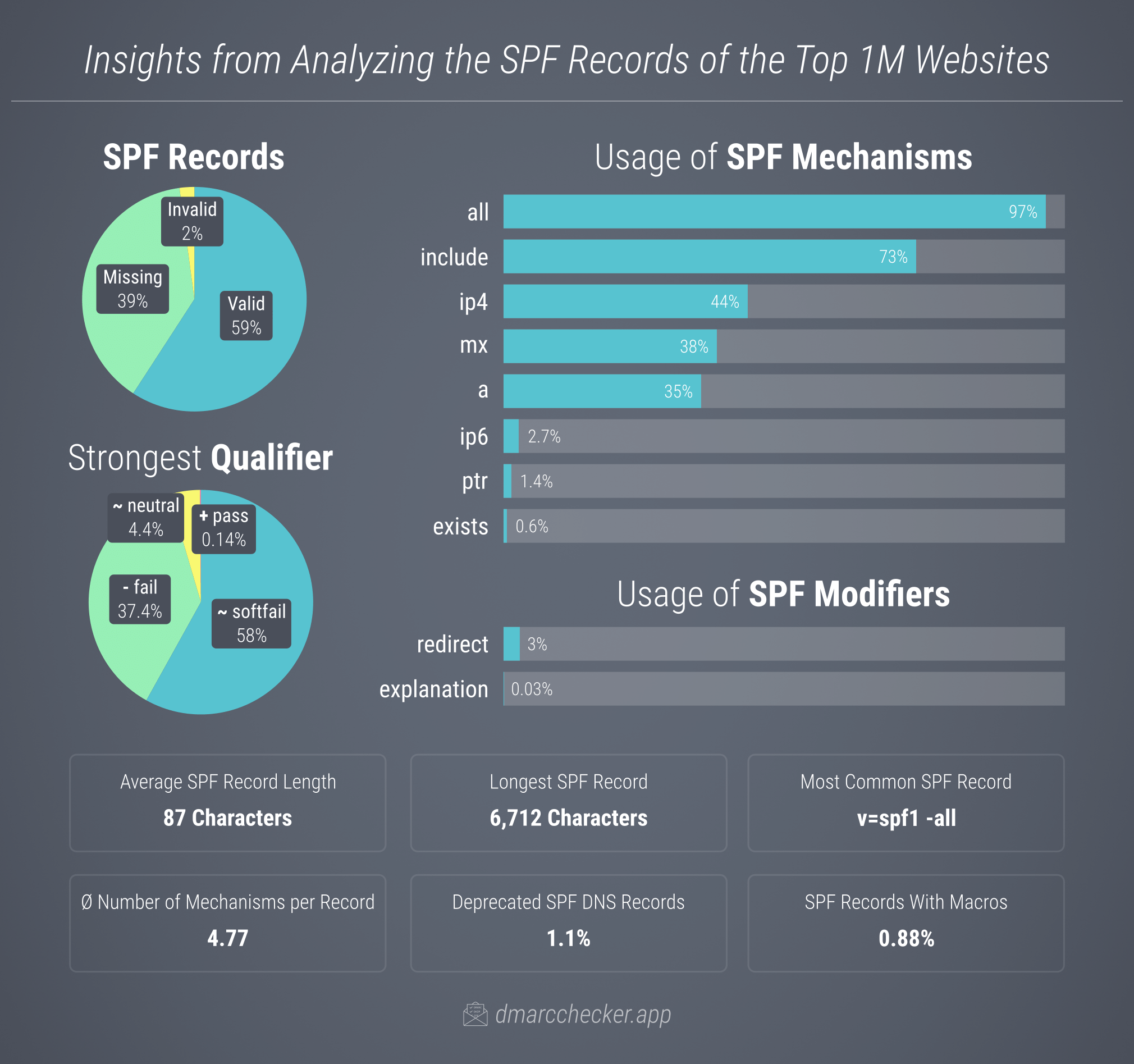
In our analysis, we found that 39% of the top 1 million domains lacked an SPF record. Interestingly, 77% of these domains were also missing MX records, indicating they are not used for sending emails. However, the absence of email activity doesn’t imply there’s no need for an SPF record. Any domain without one is vulnerable to spoofing and phishing attacks, potentially harming the domain owner’s reputation and their clients’ security. Domains not used for emailing should, therefore, have a simple v=spf1 -all SPF record, clearly indicating that no IP address is authorized to send emails on their behalf. Notable examples of domains lacking an SPF record include office.com, mysql.com, and weather.gov.
For 59% of the domains we analyzed, we discovered a valid SPF TXT record. Yet, nearly two-thirds of these records (63%) did not fully use SPF’s capacity to yield a definitive fail result, meaning they could not conclusively determine whether an IP address is unauthorized to send emails on behalf of the domain. A small fraction (0.14%) of these records were configured to always pass, effectively allowing any sender to use the domain, thus posing a significant security risk. For example, the +all directive in ubuntu.com’s SPF record (v=spf1 include:canonical.com +all) likely results from human error and should have been -all instead.
2% of the domains exhibited an invalid SPF setup resulting in a permerror. The most frequent issue was the presence of multiple SPF records, whereas only one is permitted per domain. For more details on common mistakes, refer to our 10 Most Common SPF Errors article.
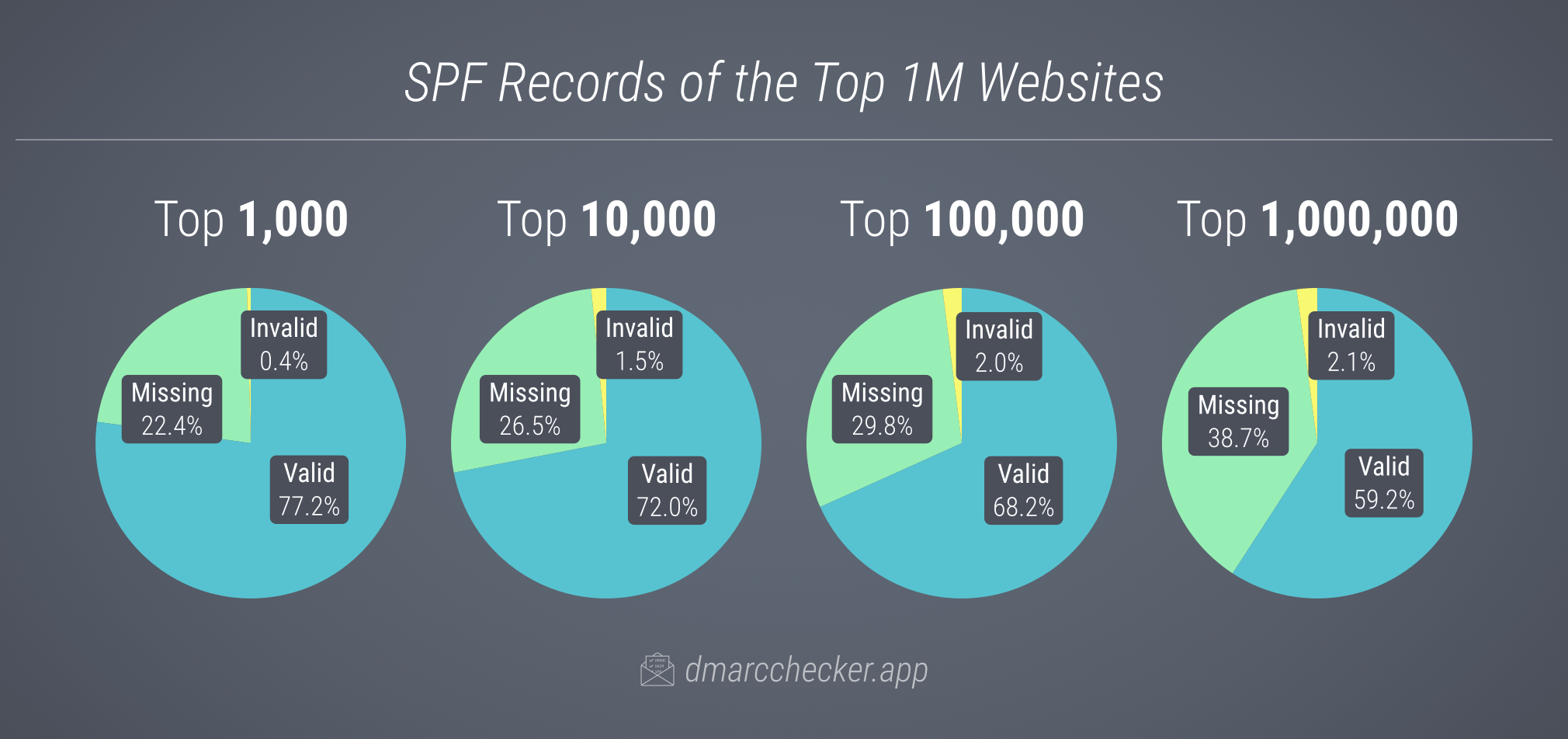
We also gathered statistics separately for the top 1K, 10K, and 100K ranked domains. As anticipated, SPF adoption was highest among the top-ranked domains, with 77% of the top 1000 domains possessing a valid SPF record. This rate gradually decreased with domain rank.
During our exploration of SPF records, we uncovered several interesting findings we wish to share:
- The domain cameron.edu has the longest SPF entry we encountered, spanning 6,712 characters and including 333
ip4and 11ip6mechanisms. For insights into why such lengthy SPF records are discouraged, see our article What’s the Maximum Length for an SPF Record?. - The most notable domain with an invalid SPF record is cloudfront.net (ranked 55). Its SPF record,
v=spf1 pjm032381tyh13bhb7nx11nytjlcjc6y -all, includes a seemingly random string, rendering the record invalid. The intention behind this remains unclear. - About 1.1% of domains still use non-TXT SPF records (resource record type 99), originally specified in RFC 4408 but now deprecated. These records are ignored by modern email servers. However, keeping both old and new SPF TXT records without synchronized updates can lead to confusion. An example is drupal.org, which has differing SPF records (
v=spf1 mx include:servers.mcsv.net -allvs.v=spf1 mx include:amazonses.com include:servers.mcsv.net -all). - 1.4% of all SPF records include a
ptrmechanism, which the SPF specification advises against due to its slow performance and the load it puts on the .arpa nameservers. A common SPF record featuring a PTR mechanism is from mx.ovh.com, which is referenced (include:mx.ovh.com) by 0.5% of domains in the top 1M. - Only 0.88% of SPF records use macros, a complex but useful feature that can help overcome the 10 DNS lookup limit. An illustrative example is salesforce.com’s SPF record,
v=spf1 include:_spf.google.com include:_spf.salesforce.com exists:%{i}._spf.corp.salesforce.com ~all, in which the%{i}macro string is dynamically replaced with the sender’s IP address.
DKIM Insights
Just taking a glance at a domain’s TXT records will tell you if SPF is set up. However, figuring out a domain’s DKIM configuration is a bit more complex. DKIM records are stored in TXT records under a specific subdomain format, like xyz._domainkey.example.com, where xyz acts as the selector and can be anything. For instance, Gmail’s default selector is google, while Microsoft 365 uses selectors like selector1-example-com, with example-com standing in for the user’s domain. Some email services also use randomly generated strings such as ug7nbtf4gccmlpwj322ax3p6ow6yfsug or date-based selectors such as 20230601 to mark when the key was generated.
This means it’s actually impossible to locate all the DKIM records for a domain and determine which ones are currently in use. To work around this, we compiled a list of commonly used selectors for our search. This approach allowed us to uncover 476,617 DKIM records across 325,923 different domains.
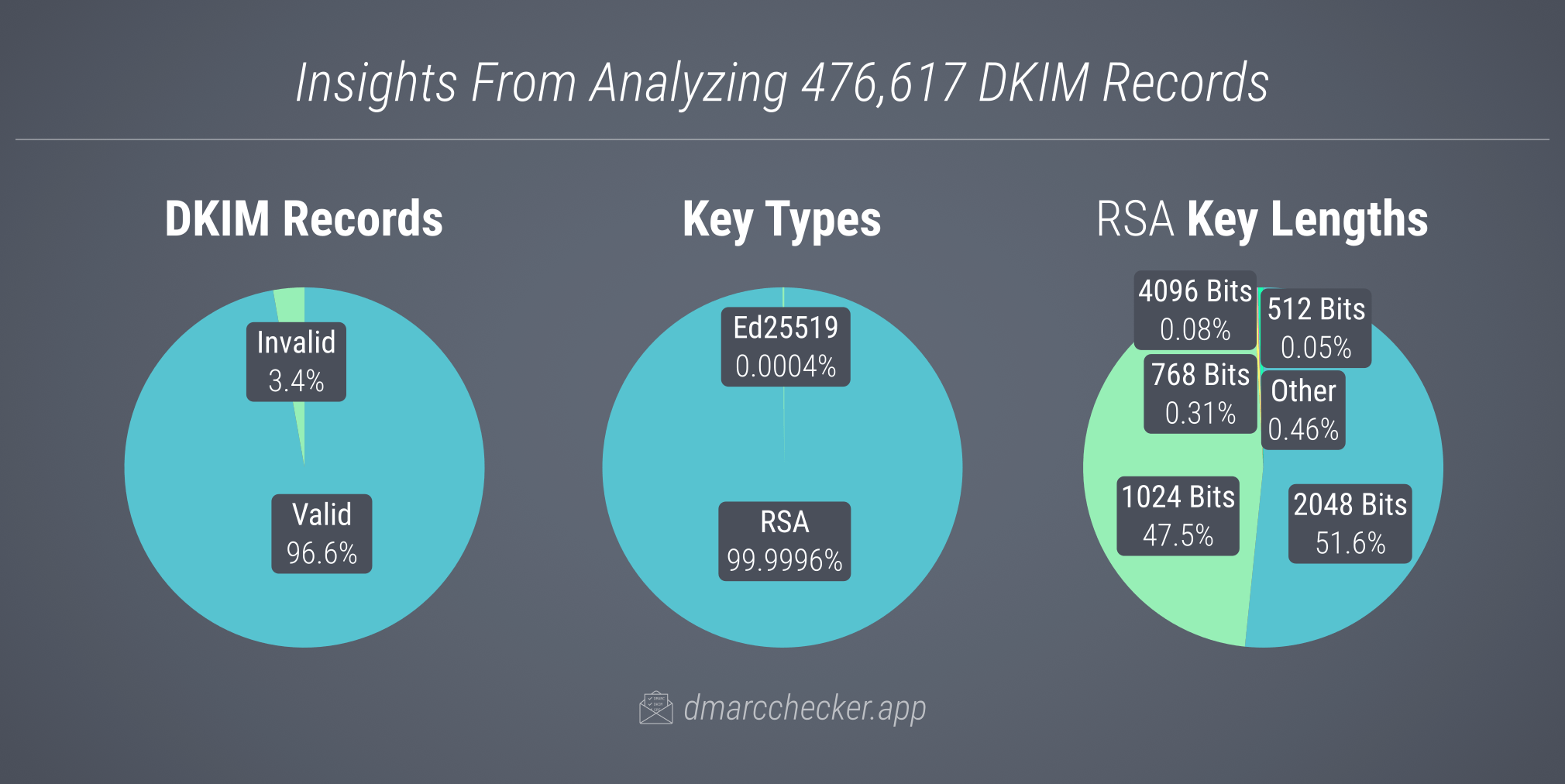
Of the DKIM records we found, 96.6% were valid. Notably, the majority employ RSA keys, with just two instances using Ed25519. Ed25519 wasn’t included in the original DKIM spec but was added in 2018 with RFC 8463. It has the benefit of having much smaller keys than their RSA counterparts, yet offers higher cryptographic strength.
Another update to the DKIM spec, RFC 8301, increased the minimum RSA key size to 1,024 bits due to security concerns over smaller keys. However, our analysis still revealed 1,726 keys below the 1,024-bit threshold. Remarkably, 68 of these keys were only 384 bits, making them vulnerable to being cracked within a few hours on modern computers. Even high-profile domains like facebook.com, glassdoor.com, and redfin.com were found to have DKIM records with RSA public keys that fall below the minimum required size.
For an in-depth look at the 3.4% of DKIM records that didn’t validate, be sure to check out our 10 Most Common DKIM Errors article.
DMARC Insights
DMARC adoption among the top 1 million websites remains relatively low, with only about one-third (33.4%) of the domains having a valid DMARC record in place. Of these, 57.2% employ a DMARC policy of none (p=none), indicating that emails failing the DMARC verification will be delivered as usual, without any particular action taken. Essentially, this means that a significant 85.7% of the domains lack effective DMARC protection.
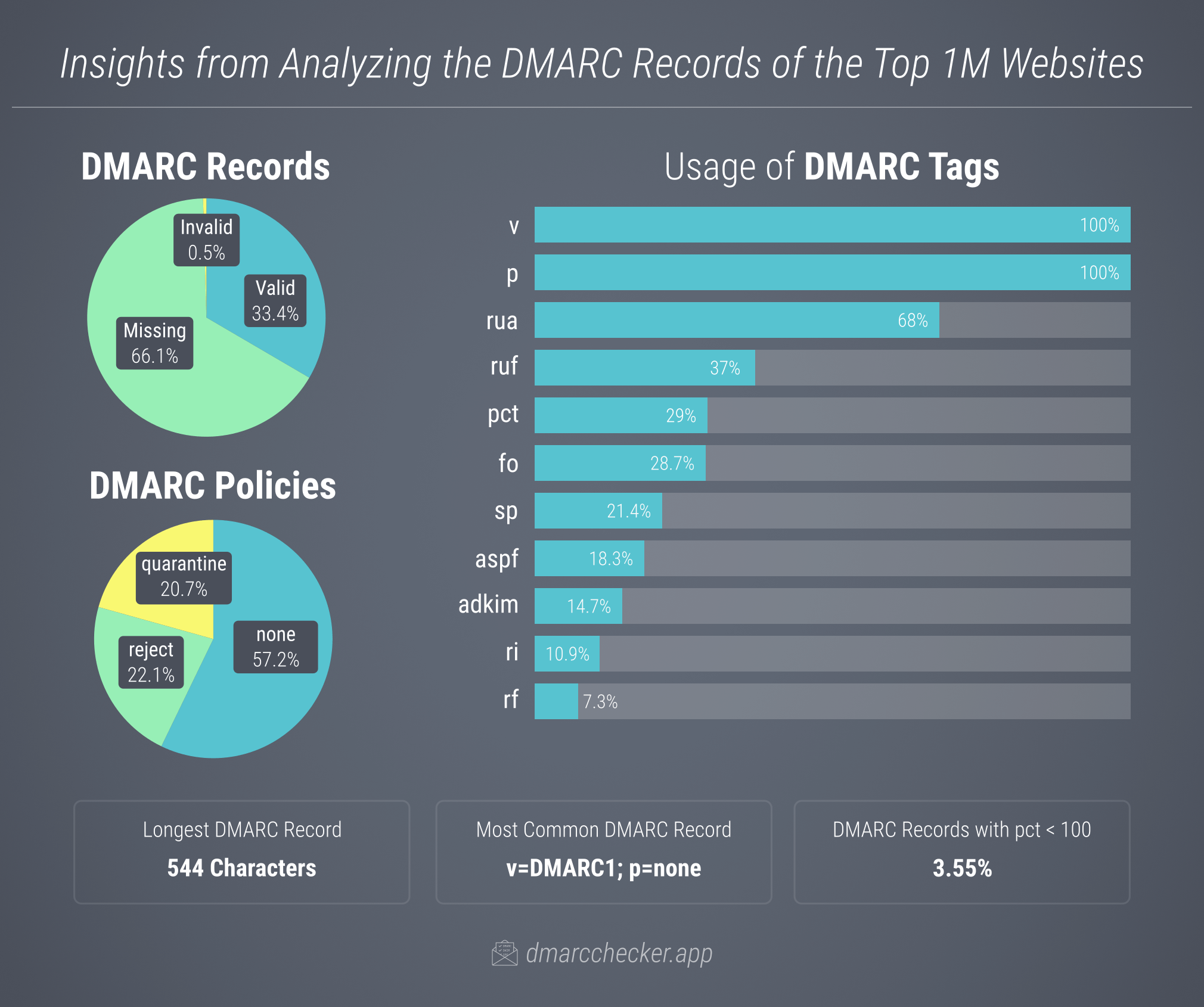
Furthermore, 69% of the DMARC records we identified include rua or ruf tags, enabling the domain owners to receive reports about emails originating from their domains. From the email addresses in these tags, we compiled a top 20 list of the most frequently used DMARC reporting services that receive and analyze these reports for their clients.
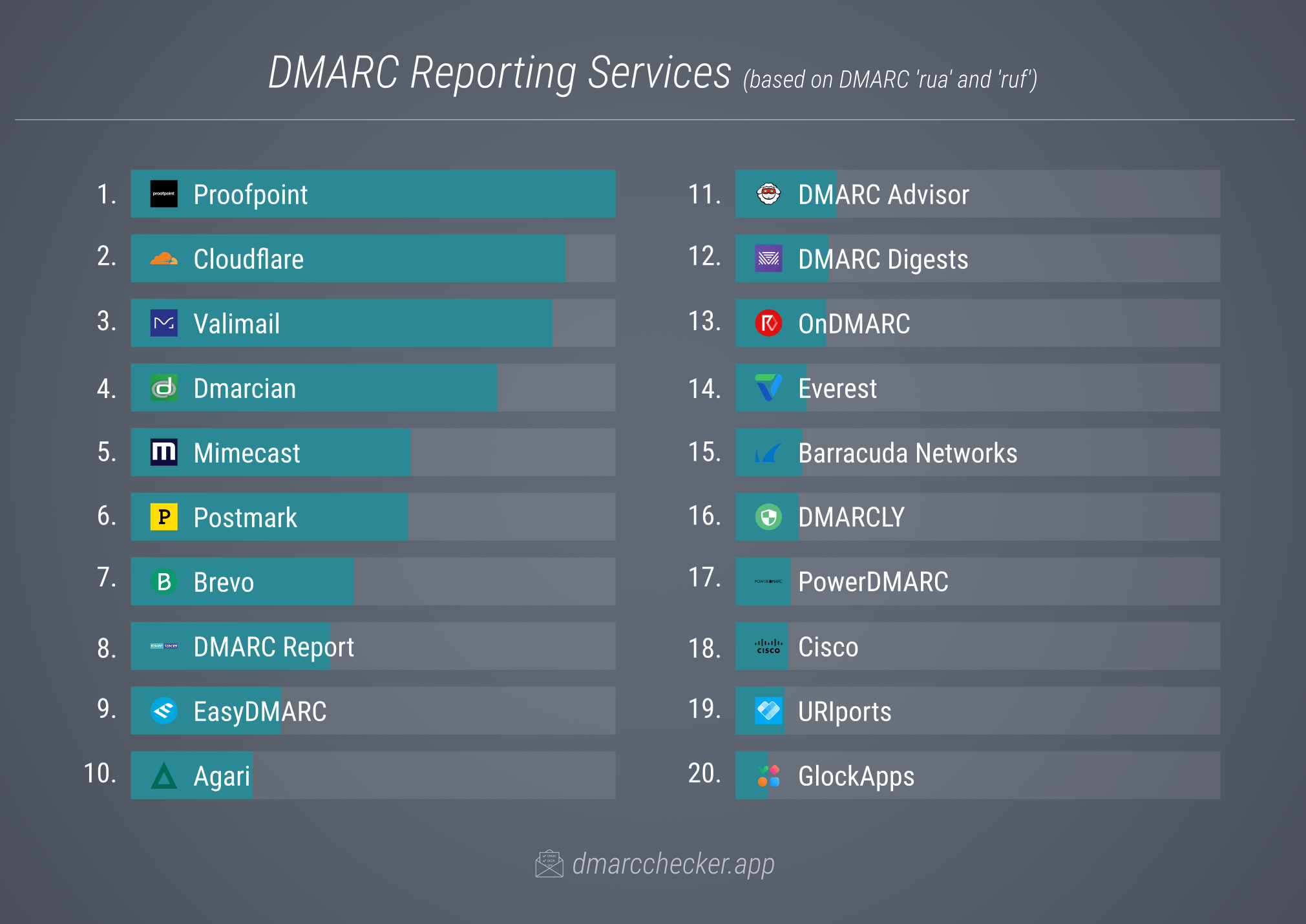
Similar to our analysis of SPF and DKIM records, we have delved into common issues encountered with DMARC records. We summarized our findings in a separate article titled 10 Most Common DMARC Errors.
Conclusion
With major email providers like Gmail and Yahoo Mail now requiring DMARC for anyone sending over 5,000 emails, we anticipated a higher DMARC adoption rate among the top million websites. It was also surprising to find that so many domains have invalid SPF, DKIM, or DMARC records. Evidently, configuring these correctly is more challenging and prone to errors than it may seem. This underscores the importance of using tools like our DMARC Checker to ensure your SPF/DKIM/DMARC setup is functioning correctly!